In this article, I will break down the following concepts
- What is Blockchain Technology
- What is a Blockchain Network
- What is Blockchain Consensus
- What is Blockchain Consensus Algorithm
Now, let's start.
When you have a group of data stored in a database managed by a party or a very small group of people, these people can choose to do whatever they want with the data. It can go to the extent of selling those data to a third party without the consent of the data owner. This practice we have seen in web 2 giant tech companies. However, this practice infuriates a lot of users in Web2 and sparks the need for a more secure, distributed, and transparent database system, which gave birth to the adoption of blockchain technology. The common use cases of blockchain technology are:
- Cryptocurrencies
- Supply chain and logistics
- Decentralized banking etc.
What is blockchain technology?
Blockchain technology is a type of distributed ledger technology (DLT) that uses a network of computers to keep a shared, decentralized record of transactions. Each transaction is validated by multiple network computers, and the validated transactions are grouped into blocks, which are then added to the chain of previous transactions, forming a permanent, unchangeable record. This enables users to trust the blockchain's data without the need for a central authority or third-party intermediary. Blockchain technology has the potential to disrupt numerous industries and alter how we exchange value and store data. The word "network of computers" gives more beauty to blockchain technology, so we can say the concept of blockchain is not complete without networks of computers, also known as a blockchain network.
What is a blockchain network?
A blockchain network is a decentralized, distributed network of computers that collaborate to maintain a shared ledger of data while using cryptographic techniques to ensure the data's integrity and security. Each computer in the network, or node, has a copy of the ledger, and the network employs a consensus algorithm to agree on the current state of the ledger and ensure that all nodes have the same data. This enables users to trust the blockchain's data without the need for a central authority or third-party intermediary.
Now, back to my analogy of a small group of people, data, and data owners. In this case, let's assume the group managing the data and the owner of the data arrive together on a decision that benefits both sides; this means a consensus has been reached. However, the decision might not favor individuals in the group, but the decision is considered an acceptable resolution.
What is blockchain consensus?
Relating the above analogy to blockchain we can denote that a consensus is also very important in blockchain technology as there is no central authority to validate what is true and what is not. A blockchain consensus can then be defined as a process by which the nodes in a blockchain network agree on the current state of the blockchain. This is an essential part of the operation of a blockchain, as it ensures that all nodes on the network have a consistent view of the data and can trust that the data on the blockchain is correct.
Furthermore, there is a scientific approach to blockchain consensus known as blockchain consensus algorithms.
What is blockchain consensus algorithm?
A blockchain consensus algorithm is a set of rules that govern how nodes in a blockchain network reach an agreement on the blockchain's current state. In different blockchain networks, various consensus algorithms are used, each with its own set of unique properties and trade-offs. Proof of work (PoW), proof of stake (PoS), and proof of authority (PoA) are some of the most well-known consensus algorithms.
Examples of Consensus Algorithms
Proof of Work (PoW)
PoW is the blockchain's first consensus algorithm. It was first implemented by the bitcoin network, and it has since been tested by other cryptocurrencies such as Ethereum, Litecoin, and Dogecoin, which use PoW consensus on their networks. PoW requires network nodes to solve complex mathematical problems in order to confirm a transaction. This is referred to as "mining." A new transaction block can only be created by one node. The winning node is then rewarded with a mining reward. Steps in PoW are described in the figure below:
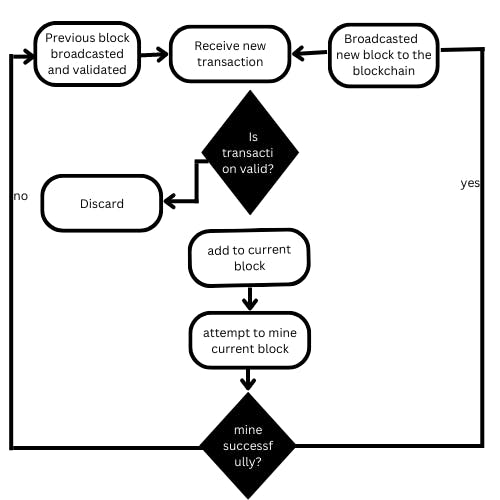
Receive new broadcasted transactions and check for legitimacy against the ledger(sender has signed the transaction and the sender address has enough balance)
Discard the transaction if it is invalid
Process legitimate transactions into the current block
Try to mine the block
If successful, broadcast the mined block to the network. Repeat the process from step 1 and mine on top of the new block
If not successful, broadcast the next block and check that the new block is successful; then go to step 1 and mine on the new block.
Proof of stake (PoS)
PoS was proposed as an alternative to PoW. In PoS, one needs to have a stake (or hold some coins) in the system to participate. In its simplest form, if you own 4% of the total stake, your chance of mining the next block is also 4%. In PoS, not much computational power is needed, which makes PoS more energy efficient. Similar to PoW, PoS is also competitive, as only one stakeholder can mine each block.
However, the main issue facing PoS is the "nothing at stake" problem. The "nothing at stake" problem is a potential issue with proof-of-stake (PoS) consensus algorithms. The problem arises when participants in a PoS system have no "skin in the game" and therefore no incentive to act honestly. In other words, because they have no inherent stake in the system, they can be malicious.
Ethereum PoS (Casper consensus) provides security to its PoS network by relying not only on rewards for security but rather on penalties.
Delayed Proof of Stake
As the name implies, staking is delegated in "Delegated Proof of Stake" (DPoS). Coin owners (or stakeholders) can elect and select leaders to stake or vote on their behalf. This is faster than PoS because there are fewer stakeholders to coordinate.
EOS makes use of DPoS; in EOS, 21 leaders (or witnesses) are elected at a time, and there is a pool of standby nodes in case one of the existing witnesses drops out or proves malicious. For producing blocks, the witnesses are paid a fee (determined by the stakeholders). In a round-robin fashion, the 21 witnesses produce blocks one at a time. As a result, a witness cannot produce consecutive blocks, making double-spending attacks impossible. If a witness is unable to produce a block within the allotted time slot, it is skipped. Witnesses who continue to miss blocks or publish invalid transactions can be voted out by stakeholders.
Because everyone gets a turn, DPoS is more collaborative than competitive. This method allows for faster blocks and scales more effectively than PoW or PoS. DPoS is also used by Steemit, Bitshares, and Lisk, in addition to EOS. This method, however, is more centralized than PoW and PoS. The 21 witnesses have the majority of control over the network. If a stakeholder has enough coins, it can vote itself in as a witness and take control of the entire network.
Proof of Burn
In Proof of Burn, you "burn" your coins by sending them to an unrecoverable address. In exchange, you will be granted the ability to mine the system based on a random selection process. In most cases, you "burn" cryptocurrency from a different chain, such as Bitcoin. The more you burn, the more likely you are to be chosen to mine the next block. This probability decreases over time, so you'll have to keep burning more coins to keep the same chance. Although the network itself does not require much energy to run "Proof of Burn," the cryptocurrencies that must be burned consume resources. This method also fails to address the issue of fairness; those with money to "burn" have a better chance of mining. Proof of Burn is used by Slimcoin and TGCoin (Third Generation Coin).
Proof of Authority
Validation in Proof of Authority (PoA) is performed by approved accounts known as validators. The transactions and blocks that are recorded on the blockchain are validated by the validators. Validators use software that automates this process, allowing them to avoid constantly monitoring their computers.
Validators must, however, ensure that their computers are not compromised or attacked. The following are the general requirements for approving a node as a validator:
It must be a verified identity that connects the node to the real world. This identity should ideally be cross-checked on a publicly accessible domain. Identity must be formally verified on-chain, with the option of cross-checking the information in a publicly accessible domain.
Becoming a validator must be difficult. This ensures that the validator values its right to validate transactions. This value should be highly valued by the validator so that it does not risk losing validator status by acting maliciously. As an example, in order to be a validator, a node must be an authorized notary.
The checks and procedures for establishing authority must be completely consistent.
By associating a reputation with an identity, validators are incentivized to uphold the transaction process because they do not want their identities to be associated with a negative reputation, thereby losing their hard-earned validator role. This method is centralized because an authority must vet and admit validator nodes. As a result, it is commonly used in private and permissioned blockchains. Because no computation is required, PoA is much faster than PoW. VeChain, POA Network, and the Ethereum testnets Kovan and Rinkeby all use it.
Delayed Proof of Work
Delayed Proof of Work (dPoW) is a type of hybrid consensus. It makes use of the hashing power of a secondary blockchain to provide additional security for the primary blockchain.
Komodo uses dPoW by connecting to the Bitcoin blockchain. Notary nodes transfer data from the primary blockchain to the secondary blockchain. Komodo supports either PoS or PoW on the primary blockchain and only works with PoW secondary blockchains. To tamper with a transaction on the primary blockchain, the data on the secondary blockchain must also be changed. As a result, Komodo can rely on the larger Bitcoin blockchain's security to keep its data immutable.
Directed Acryic Graphs
Directed acyclic graphs (DAGs) are broad forms of blockchain that can be used in different networks. Because the DAG structure allows transactions to be added in parallel, it is highly scalable.
Most blockchain systems we've looked at with a linear structure add blocks to the blockchain one by one. As a result, blockchains are inherently slow. Each block or transaction in a DAG confirms a number of previous blocks. Despite being regarded as the next-generation blockchain structure, one of the main issues with DAGs is that smart contracts are typically implemented through oracles rather than being directly deployed on chain.
Conclusion
Consensus algorithms play a critical role in ensuring consistency and accuracy on a blockchain or distributed ledger. Understanding how different types of consensus algorithms work would allow us to appreciate blockchain-based applications, assets, and investments and make informed decisions. Finally, the choice of consensus is determined by the network implementer's goals. It could be for a self-governing decentralized public system or an enterprise consortium blockchain handling sensitive transactions.
As we learn more about how network participants respond to various incentives, the field of consensus algorithms continues to evolve (especially for cryptocurrencies). With a wide range of blockchain use cases emerging, we can expect a wide range of consensus methods to be used. Because of the variety of blockchain solutions, any blockchain network may be required to communicate with several others; interoperability will become a critical consideration.